Sextortion scam – a follow up.
 This time last month I posted about a sextortion scam that was sending out large amounts of emails to people claiming to have recorded them watching porn. As proof that they meant business, they included an old password the victim had previously used. There have been some developments.
This time last month I posted about a sextortion scam that was sending out large amounts of emails to people claiming to have recorded them watching porn. As proof that they meant business, they included an old password the victim had previously used. There have been some developments.
The first thing to highlight is that the evil doers are now using partial telephone numbers in this sextortion scam instead of old passwords. This can be more effective than the old password ruse that was used last month. This could be because many people may have changed passwords since. However not too many of us regularly change our mobile number.
New development of the sextortion scam
We may also be quite used to seeing our number appear in a partially redacted manner.
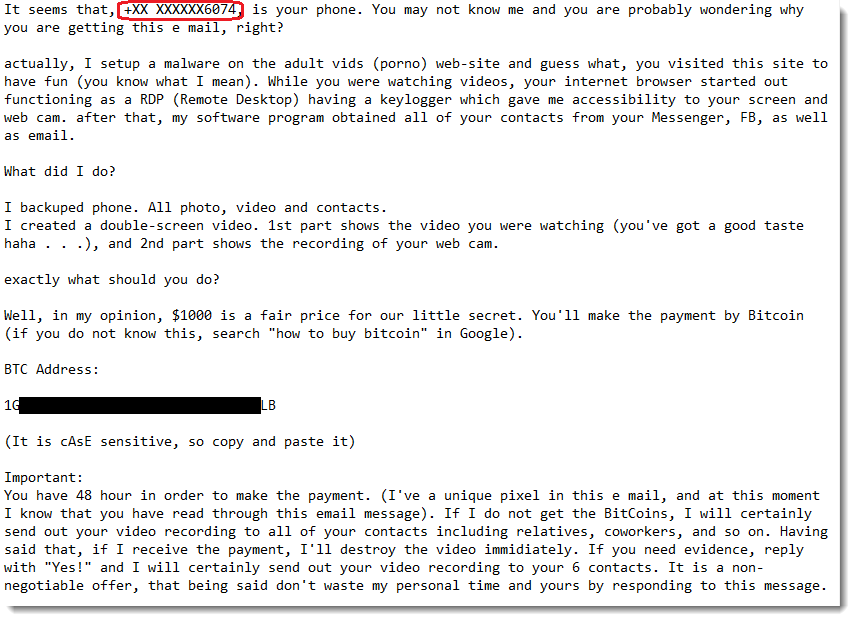
So in this example, the victim sees the number +XX XXXXXX6074 instead of an old password. They have confirmed to the good folks over at the Internet Storm Centre (ISC) that those last 4 digits match their number. So that can really make people sit up and take notice.
The question arises though – why are they partially redacting the number? It’s not like these guys are reputable and are trying to protect your privacy by not emailing the full number. If they truly had your full information from a hack or a data breach, why not just put the whole thing in there? It would be very much more effective.
No, they don’t have your full number at all and as surmised by the team over at the ISC, they are probably getting the information from password reset forms. This is where the like of Google and Amazon will send you a text message with a code as part of the reset process. Or as part of a two-factor authentication step such as the following:
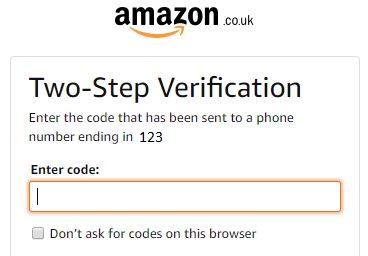
So the bad guys have upped their game here. Just don’t fall for it.
Are they making any money?
The other update in relation to this is about the money they have actually made from this sextortion scam. A couple of weeks ago the fine people at the ISC did an analysis of the bitcoin wallets that were included in the scam emails. These are the long string of characters and numbers that I redacted in the email example above.
“Wait a second” I hear you say, “Bitcoin is untraceable, anonymous money.”. Actually it’s not really untraceable as by the very nature of the blockchain on which bitcoin is based, each transaction is fully public. It would be more appropriate to say that it is unregulated money.
Anyway, their analysis revealed that of the many wallets they were monitoring:
- 123 payments were received
- $235,000 in total was paid to those wallets
- $4,900 was the biggest payment, with an average payment of $1,900
This was probably a subset of all the wallets in use across the whole campaign. However you can see that people were fooled into parting with their money in reasonably large numbers.
So you now want to easily protect you and your staff from these kind of scams, right? I do some pretty awesome security awareness training. If you were interested in finding out more, just send an e-mail to info@L2CyberSecurity.com.
#LetsBeCarefulOutThere
#SecuritySimplified
