Is somebody else using your password?
 Is somebody else using your password? If your password is “123456”, then absolutely yes. Nearly 21 million other accounts use that same password. But how about “Gobbledegook”? That password is actually used by at least 9 other accounts. “LiamIsANiceHelpfulCyberSecurityPerson” has not been used before – I might use it for myself. ?
Is somebody else using your password? If your password is “123456”, then absolutely yes. Nearly 21 million other accounts use that same password. But how about “Gobbledegook”? That password is actually used by at least 9 other accounts. “LiamIsANiceHelpfulCyberSecurityPerson” has not been used before – I might use it for myself. ?
So how do I know these things? Where am I getting this figures from. Well just like November where I told you about the free Quad 9 service, which prevents you going to know evil sites or in December where I told you about the free Security Planner tool, which gave you simple advice on how best to protect your particular set-up, this month I give you the free Pwned Passwords tool, which was developed by highly respect security researcher Troy Hunt. Before you leap to the comments section highlighting my atrocious spelling – that’s how it is spelled – pwned is a computer gamer term for being completely dominated or compromised and is pronounced “powned” (to rhyme with “owned”).
So how does this pwned password tool answer the question is somebody else using your password? It’s quite simple, the Troy has got copies of online account information (including passwords) that has been breached from various sources over the last number of years. He has 500 million passwords on his database. Now he doesn’t have the passwords linked to their associated account, such that if he was hacked that somebody would get access to his juicy treasure trove of account information, it’s simply a database of passwords. He has used a certain very secure methodology to test the passwords, but there is no point in going into it here. If you’re a nerd with an itch to scratch, then you can read all about his methodology here.
So how should you use this tool? Simple go to the Pwned Passwords page and type in your various passwords. Here is the result for “123456”:
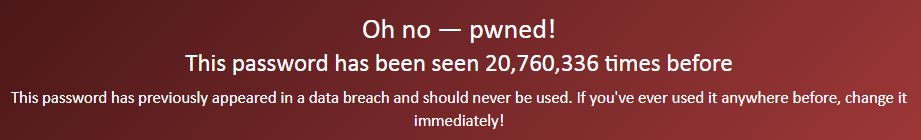
And the result for “LiamIsANiceHelpfulCyberSecurityPerson”:
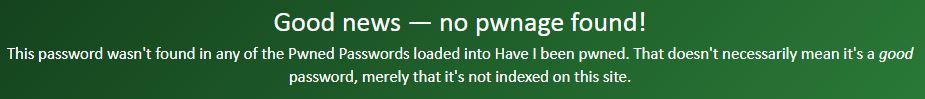
So what should you do if your password has been used before, particularly where it has been used a LOT? It’s kind of obvious, but you need to change it. Yes, I know it’s a pain. Yes you might forget what you changed it to. Guess what? When you change it, write your new password down on a piece of paper and put it in your drawer or maybe your wallet/purse. ?
No I haven’t taken complete leave of my senses. But this is a case of risk reduction. Sure, you have an open copy of your password in a public-ish place, but it’s not going to be there forever. You will consult this piece of paper regularly in the first 3-4 days after changing your password. As your muscle memory starts to kick in, you will consult it less and less. After a week to 10 days you probably won’t be using the piece of paper anymore, so at that point you can destroy it.
Keeping this reminder of your password to hand will also enable you to do one more brilliant thing with your password and that is to make it LOOOOOONNNNNGGGGG. Don’t use “LiamIsANiceHelpfulCyberSecurityPerson” because that’s mine ? but either use a long passphrase (a sequence of words like my example) that is at least 15-20 characters long or use a password manager to generate a long nonsensical password which it has to remember, but you don’t. You only have to remember the master password, which you will have made it long and complicated. More details about passwords can be found under Commandment 8, including talk about password managers.
Actually, one of the other really cool things Troy has done was to enable developers to create plug-ins that can query his database of passwords. One of the password managers (1Password) has incorporated this functionality into it’s product, so if you chose a password that has been pwned, it will be flagged to you.
Finally, it would be remiss of me not to point out the main feature of Troy Hunt’s site. This has been around for many years and it’s the Have I been pwned? feature. All you do is put in your e-mail address(es) or User IDs and it will tell you if they were part of a data breach of some online service. He has details on nearly 5 billion breached accounts, so it’s pretty comprehensive.
