Dodgy extensions and not a builder in sight.
 A lot of normal people might think about the phrase “dodgy extensions” and associate it with some kind of cowboy builder. But alas, the dodgy extensions to which I refer are in a web browser and these could lead you to a data breach or worse. This has come to light recently when a browser extension for a popular cloud storage service called Mega.nz was compromised and started passing people’s User IDs and passwords to an evil doer’s server based in the Ukraine. This is similar to the breach in April where Saks and related stores in the US had their point-of-sale terminals compromised.
A lot of normal people might think about the phrase “dodgy extensions” and associate it with some kind of cowboy builder. But alas, the dodgy extensions to which I refer are in a web browser and these could lead you to a data breach or worse. This has come to light recently when a browser extension for a popular cloud storage service called Mega.nz was compromised and started passing people’s User IDs and passwords to an evil doer’s server based in the Ukraine. This is similar to the breach in April where Saks and related stores in the US had their point-of-sale terminals compromised.
What is an extension?
These are little pieces of software that are available for internet browsers to provide some type of add-on or extra functionality. There are thousands of these kind of things out there and you might have some installed without realising it. One quick way is to look at the top of your browser window, on the right-hand-side of the address bar, there may be a few icons. Here is an example from my Chrome browser:
![]()
These extensions are:
- LastPass (password manager)
- Privacy Badger (blocks tracking cookies)
- F-Secure Browser Protection (adds security for online banking pages)
- HTTPS Everywhere (forces browser to use HTTPS version of websites where possible)
All security related for some reason. ?
Not all installed extensions may be shown on the browser bar. They may also be hidden, but still enabled. In order to find out what extensions you have, do the following:
- Google Chrome – paste the following address into a new tab chrome://extensions/
- Firefox – paste the following address into a new tab about:addons
- Edge – Click the three horizontal dots (top right of the browser) -> Extensions
If you have a lot of extensions, then you have a greater chance of falling victim to the bad guys.
How do we get dodgy extensions?
Most of the extensions you have are probably all legitimate and from a reliable source … originally. However, over time the developers of these extensions may sell them on or even just give up on them and somebody else takes control of the extension. In the case of the Mega.nz extension, the person responsible for the software was compromised. The extension was then infected for a period of time and it joined the ranks of the dodgy extensions.
The software started stealing users log-in IDs & passwords and sending them onto the criminals. To do this, it required additional permissions on the users browser, which unwary people granted. If you’ve used an extension that is actively being enhanced, you will regularly sees notifications that it has been updated. In the Mega.nz case, when the notification was issued, there was also a notice about the additional permissions that the evil doers needed to be granted in order to steal passwords.
Here is an example of the permissions needed by LastPass:
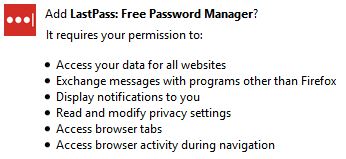
Those are already pretty extensive. If that suddenly required additional permissions, most people might tend to just click OK to “get on with it” and not stop to think “Why is this asking for enhanced permissions?”
What should I do?
If you have been using your computer for a while, you may have accumulated more and more extensions. So review all of the extensions you have. Remove those that you no longer use or don’t need.
You should also put in place controls on your staff, to prevent them from installing dodgy extensions. You don’t want them causing any kind of data breach which might fall into the auspices of the #GDPR.
If and when an extension gets updated, if it asks for additional permissions, always deny them. Then seek an expert opinion. An actual expert and not your 15 year old computer mad niece/nephew. You could send us details of the extension and what permissions it wants at info@L2CyberSecurity.com and we will answer free of charge.
If you would prefer a security review of your set-up we would be happy to arrange that too. Call us on 087-436-2675.
